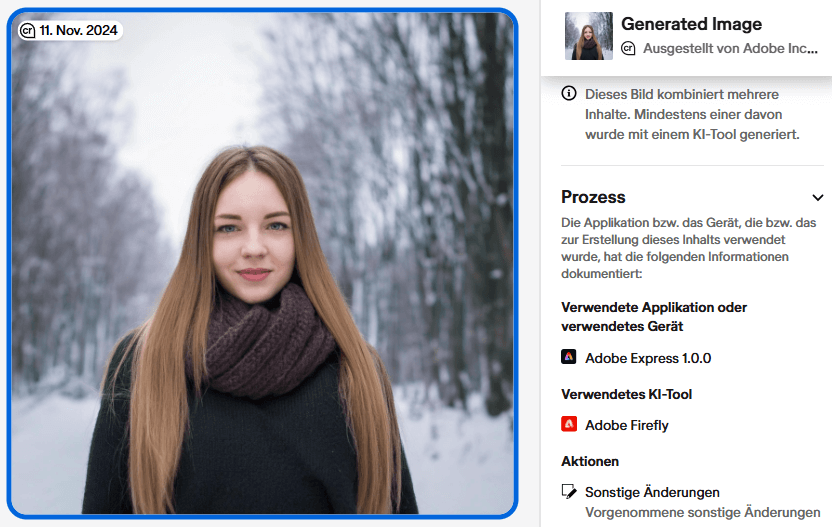
The proof of origin via digital signatures is subject to similar limits as other documentation or DRM measures. As soon as screenshots or screen recordings of content are made, conversions to other formats are carried out or the corresponding metadata is deliberately removed, the resulting file can be redistributed on the Internet without any reference to its source.
Nevertheless, the oldest online source can often be found via a reverse search. E.g. for an image of which it is not known whether it is a real photo or not. If this file contains valid C2PA camera data, all the better. However, this does not mean that you can trust the information found one hundred percent. The cryptographic integrity of a signature simply does not provide any proof that an authentic representation of reality exists. With camera firmware developed according to C2PA specifications, it would also be possible to store and sign AI-generated images, for example. Metadata could also be freely invented and properly signed. Strictly speaking, an intact C2PA structure simply means that the file and its metadata have been signed by the specified entity and have not been altered since.
Conclusion: C2PA technology makes targeted manipulation more difficult, but of course cannot prevent it completely.

 https://www.teamnext.de/wp-content/uploads/2024/10/geodaten-dam.jpg
720
1800
Björn Buxbaum-Conradi
https://www.teamnext.de/wp-content/uploads/2022/03/teamnext-mediahub-logo-bunt.svg
Björn Buxbaum-Conradi2024-10-14 14:12:582024-11-28 15:29:55The importance of geodata in media management
https://www.teamnext.de/wp-content/uploads/2024/10/geodaten-dam.jpg
720
1800
Björn Buxbaum-Conradi
https://www.teamnext.de/wp-content/uploads/2022/03/teamnext-mediahub-logo-bunt.svg
Björn Buxbaum-Conradi2024-10-14 14:12:582024-11-28 15:29:55The importance of geodata in media management